이 게시물은 아래 강의를 참고 하였습니다.
참고 강의 https://www.youtube.com/watch?v=KdATmTulf7s&list=PLApuRlvrZKojqx9-wIvWP3MPtgy2B372f&index=1
문제)
- Create a new ClusterRole named deployment-clusterrole, which only allows to create the following resource types: Deployment StatefulSet DaemonSet
- Create a new ServiceAccount named cicd-token in the existing in the existing namespace apps.
- Bind the new Cluster Role deployment-clusterrole to the new ServiceAccount cicd-token, limited to the namespace apps.
풀이)
1. Service Account 생성
https://kubernetes.io/docs/reference/generated/kubectl/kubectl-commands#-em-rolebinding-em-

$ kubectl create serviceaccount cicd-token -n apps
2. ClusterRole 생성
https://kubernetes.io/docs/reference/access-authn-authz/rbac/#kubectl-create-clusterrole

$ kubectl create clusterrole deployment-clusterrole --verb=create --resource=Deployment,statefulset,daemonSet -n apps

3. ClusterRole binding
https://kubernetes.io/docs/reference/access-authn-authz/rbac/#kubectl-create-rolebinding

kubectl create clusterrolebinding deployment-clusterrole-binding --clusterrole=deployment-clusterrole --serviceaccount=apps:cicd-token -n apps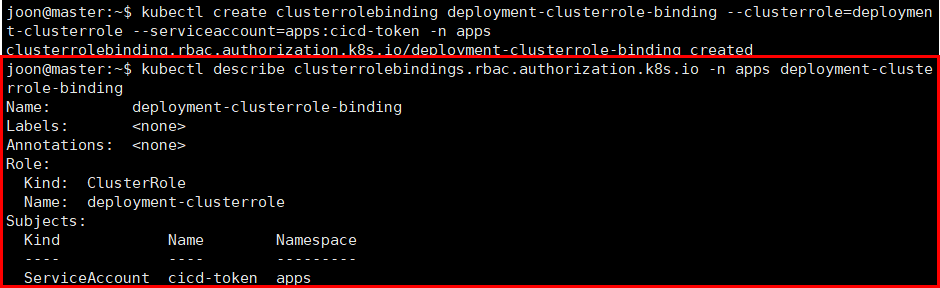
'k8s' 카테고리의 다른 글
| CKA 준비 (30) Network Policy (1) | 2022.09.25 |
|---|---|
| CKA 준비 (29) Kube-DNS (0) | 2022.08.30 |
| CKA 준비 (27) ServiceAccount Role binding (0) | 2022.08.17 |
| CKA 준비 (26) User Cluster Role Binding (0) | 2022.08.01 |
| CKA 준비 (25) User Role Binding (0) | 2022.07.26 |